Microsoft has numerous Office 365 security features built in to help you monitor activity, protect data, identify threats, and manage identity, access, and privileges. But getting the most out of those tools can be difficult, particularly for mid-sized organizations. Integrating them with data from other sources in your network and cloud is even more challenging.
In this post, the first in a series, we’ll discuss two important initial steps you can take to secure your Office 365 deployment:
- Get visibility into what’s happening in Office 365 without getting lost in the noise; and
- Govern user activity with sound Office 365 identity, access, and privilege management practices.
Although we’ll focus on how mid-sized organizations can extend their existing Office 365 security tools and practices, these tips can apply to most organizations.
Office 365 Security: A Growing Need
Microsoft continues to march forward with its transformation from an enterprise software company to a cloud company. Growing Microsoft Office 365 adoption is one of the most visible signs this strategy is working. Many companies started down the path by begrudgingly accepting Office 365 as a new way to license Office applications. Now they’re embracing cloud-based group collaboration with tools like OneDrive for Business and Microsoft Teams.
It’s not just small companies driving Office 365’s advance. Large enterprises like Eli Lilly and Goodyear are now using Office 365. Even Microsoft Teams, which is less than two years old, is now used by 87 of the Fortune 100.
Of course, this dramatic shift in how businesses communicate and manage content introduces a host of new information security and compliance challenges. To its credit, Microsoft has invested heavily in Office 365 security features through a mix of in-house development and acquisitions. But in many ways, the sheer breadth of components – and security features – that Office 365 includes makes it difficult for security teams to wrap their arms around the problem.
Want to learn more? Schedule a demo of our ActiveEye Office 365 security solutions with one of our security specialists.
Implementing 24×7 Office 365 Activity Monitoring
Microsoft offers a wealth of information about what’s happening in Office 365 through standard web-based reports with high-level summaries. The real treasure trove, though, is the Office 365 Management Activity API. You can use this API to get extensive information about user and administrator activities, platform operations, and security activity available through a representational state transfer (REST) web service.
Applied effectively, this information can play a central role in your Office 365 security monitoring and response strategy. But the time and resources it takes to acquire, harmonize, and derive value from this information isn’t practical for many organizations. This is particularly true for mid-sized companies with limited IT and security resources.
Third-party partners like Delta Risk can add significant value in this area by ingesting this information on behalf of your organization, then applying a layer of security policy logic, automated analysis, and human analysis. This brings important security insights to the forefront so you can initiate timely security response workloads as needed.
Managing Identity, Access, and Privileges
The principle of least privilege – the practice of giving user accounts only those privileges that are needed to perform their designated function – is a longstanding cornerstone of information security. This concept is particularly important when moving to Office 365, which is much more dynamic than traditional on-premises communication and document storage infrastructure. It’s also important to pair identity-centric privilege management with strong authentication, given the Internet-centric nature of Office 365.
Organizations that have built their authentication and privilege management function around Microsoft Active Directory for their on-premises environment can find a relatively smooth migration path to Microsoft’s own identity-as-a-service (IDaaS) offering, Azure Active Directory (Azure AD). Azure AD includes components that synchronize with an existing on-premises directory to support hybrid environments. Microsoft added more advanced native privileged access management policy features last year for organizations with more sophisticated needs in this area.
Organizations with more of a cloud-first mindset and a preference for something simpler than Azure AD may also choose from a number of well-regarded third-party IDaaS providers, including Delta Risk’s partner Okta, and explore how cross-vendor privilege management solutions from vendors like CA Technologies and CyberArk may be extended to the cloud.
Microsoft often requires add-on licensing for its integrated security features, so third party options warrant consideration. In some cases, they may offer better return on investment and provide a more cohesive approach across cloud providers. The other option is to have us manage this for you, so you don’t have to worry about adding yet another vendor to your list of things to manage.
Making Office 365 Security Information Actionable
Actively monitoring, investigating, and responding to the full array of Office 365 security events is challenging to implement and scale. This is particularly true in mid-sized organizations with limited IT and security resources. The volume of data can be overwhelming. But surfacing the anomalies and policy violations hidden in this sea of data is a critical element of a comprehensive Office 365 security strategy.
The value of Office 365 security information is also amplified when it is combined with other information sources, such as other cloud service APIs, endpoint security information, and security information and event management (SIEM) system data.
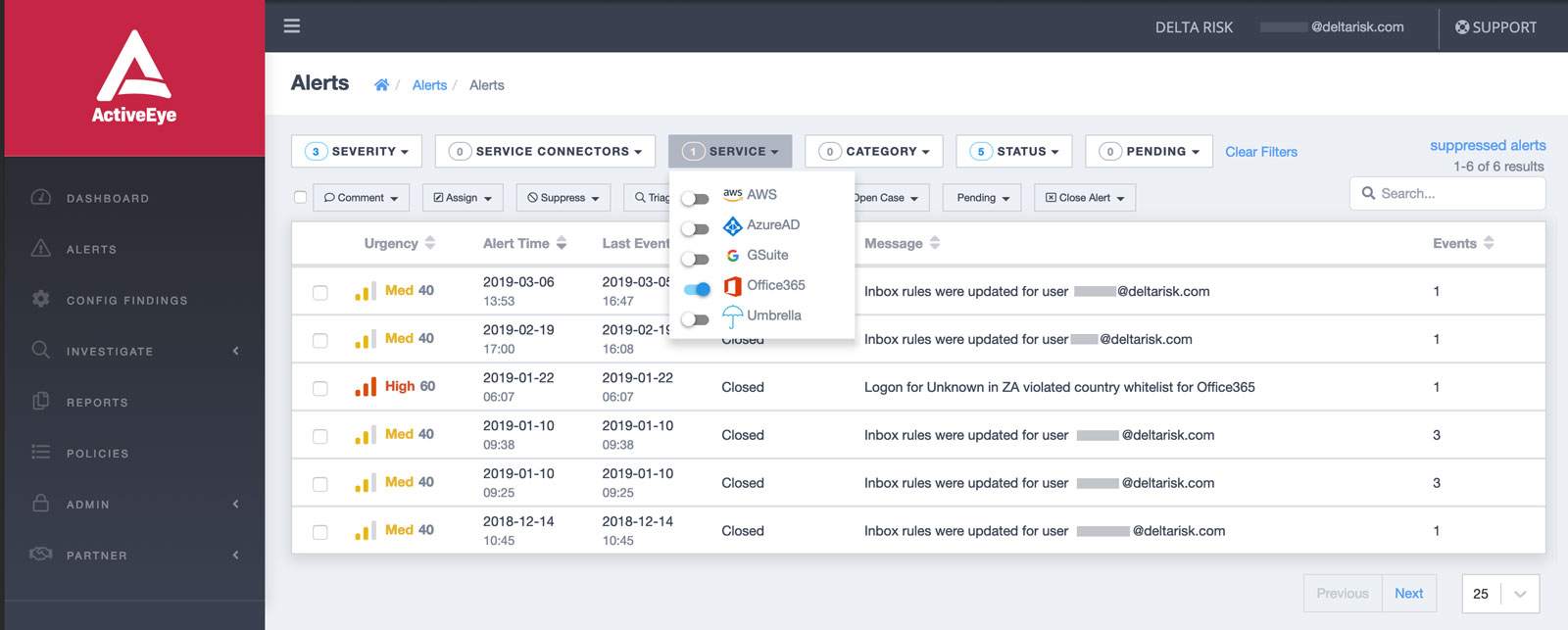
THE ACTIVEEYE PORTAL ENABLES YOU TO DRILL DOWN TO SEE ALERTS RELATED TO OFFICE 365 AND PRIORITIZE THEM, OR YOU CAN GET ALERTS VIA SLACK AND TEAMS.
Summary
Unlike the cloud access security brokers (CASBs) that many large enterprises have adopted, Delta Risk provides more than self-service information and tools for your already over-taxed team to setup and use. Our service includes 24×7 monitoring and co-management from a team of security experts who function as an extension of your in-house security team. This brings the essential disciplines of Office 365 security together into a unified, cost-effective framework that doesn’t place more burden on your in-house team as cloud usage grows.
In future posts, we’ll take a closer look at other key Office 365 security disciplines like external threat protection and data protection.
