In today’s post we’ll discuss Google G Suite security best practices and some proactive steps you can take for a security tune-up. None of these recommendations are particularly hard to implement. But cloud security requires a different mindset than traditional security operations, so even savvy security teams often overlook them. We’ll also take a look at how a SOC-as-a-Service solution can help.
Most G Suite security best practices focus on topics like 2-step verification, app and file sharing activity reports, user account administration, and monitoring. In our last article on this topic, for example, we shared some common pitfalls that G Suite administrators should avoid. Making your Google cloud environment more secure isn’t just about avoiding mistakes, though.
Learn how to get the most from native G Suite security features with ActiveEye.
Rethink the Role of a SOC
Historically, security operations centers (SOCs) have been optimized for monitoring on-premises network and data security devices. Devices like firewalls and intrusion prevention systems are as important as ever. But protecting Software-as-a-Service (SaaS) platforms like G Suite requires a much different skill set, methodology, and toolset. There are a few ways to deal with this challenge, each with varying degrees of difficulty.
One option is to collect all the security event information from G Suite through APIs. Simply adding this raw data feed to an existing SOC workload, though, isn’t an effective approach. You need a SOC, to start, along with specialized knowledge about the nuances of each cloud platform to interpret and respond to threats effectively to protect sensitive information and prevent data loss.
If you have a SOC (and most SMBs don’t), another possibility is to enhance your existing capabilities by adding G Suite security experience. You could do this by training existing employees, hiring new people with those skills, or a combination of both. This isn’t a quick fix, though, by any means, and it’s not that easy to find people with these skills or make time for training.
You can also invest in tools like cloud access security brokers (CASBs) to give your security analysts more information and control. However, at the rate SaaS platforms are being adopted in most organizations, a full-blown CASB solution can be fairly expensive and time consuming.
One solution that’s working well for many organizations, particularly SMBs, is SOC-as-a-Service. A modern SOC-as-a-Service vendor can take care of your cloud monitoring and G Suite security needs much more effectively and economically. As a result, deciding whether to build and staff an in-house SOC or use a managed security services provider (MSSP) is no longer an all or nothing decision. In today’s hybrid cloud environments, a blended approach often makes the most sense. In-house teams can maintain lead responsibility, but partners can act as a force-multiplier with a co-managed solution.
Instead of an unfiltered G Suite security data feed, for example, your in-house team will only get prioritized incident reports. Limiting reports to actionable insights on a potential threat gives your in-house team more time to focus on the things that really matter. In addition, on-demand access to subject matter experts who are up to speed on G Suite security best practices also reduces the need to hire more people as new SaaS services are adopted.
Continuously Improve the Signal-to-Noise Ratio
One problem that nearly all SOCs face is information overload. Security products, network devices, endpoints, and cloud platforms send ever-growing waves of data. There are valuable insights hidden in this data. But tuning the signal-to-noise ratio is a never-ending challenge. If you make the focus too narrow, you can miss critical events. If you make the focus too wide, though, you can get overwhelmed with many false positives, which leads to “alert fatigue.”
This is another area where teaming with a SOC-as-a-Service partner like Delta Risk can help. Our cloud-based ActiveEye platform analyzes G Suite security events alongside any other cloud platforms you’re using, as well as your network and endpoint security. ActiveEye applies advanced machine learning to surface the security incidents that matter most. It can also be combined with a full or partial SOC-as-a-Service model to add human analysis and insights, as well as professional services like incident response.
One of the ways that ActiveEye helps to cut through the noise is the Virtual Analyst. The Virtual Analyst applies machine learning to the alarms and outcome history of our SOC team. It then makes recommendations based on these alarms and in some cases automatically increases or decreases the prioritization of alarms based upon history.
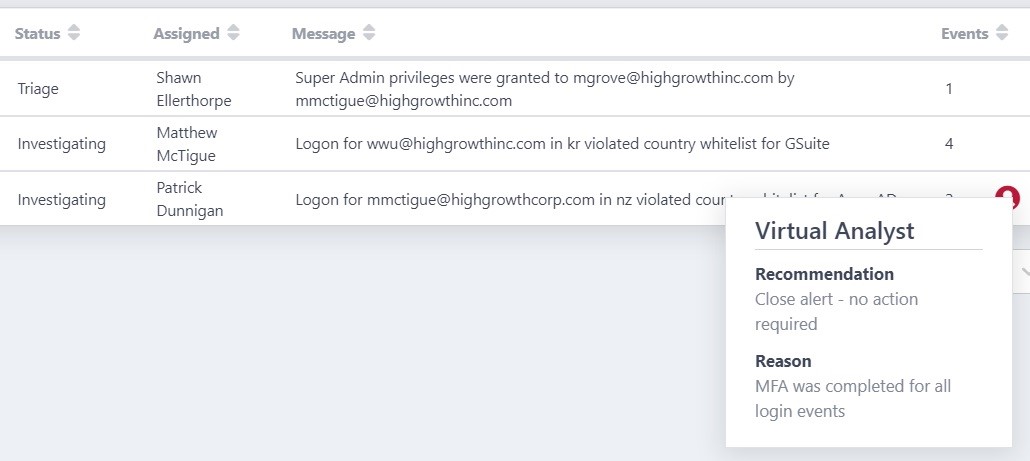
The graphic below shows the activity of the Virtual Analyst for a given customer in a month.
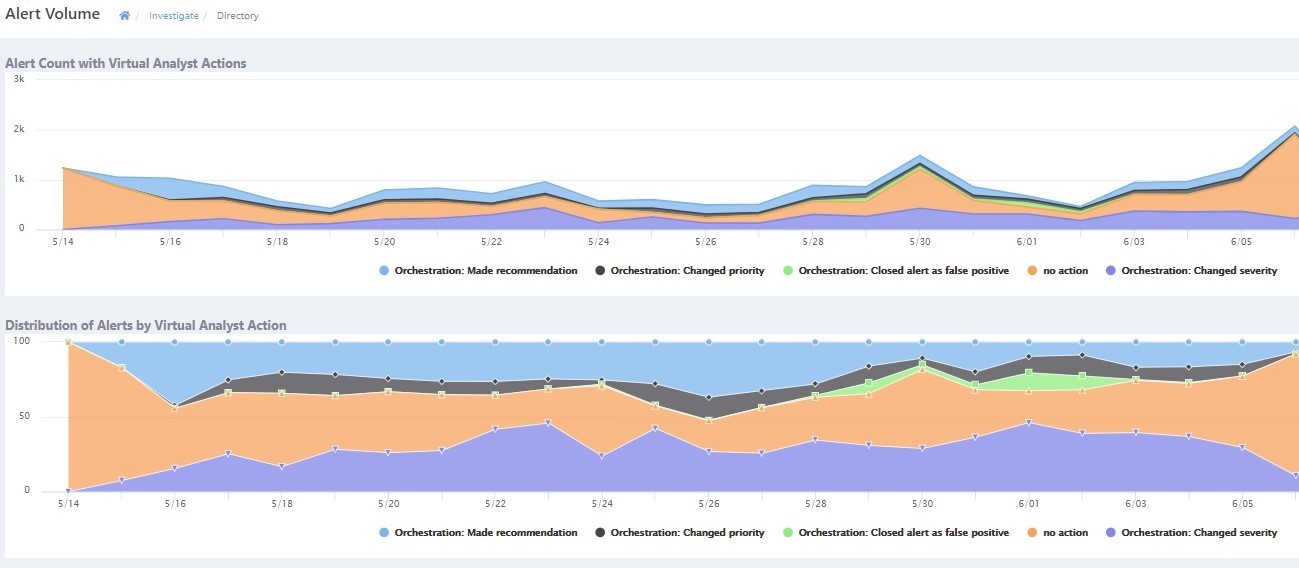
This type of automated assistance is essential, as the rapid growth of SaaS usage and new security feeds are making the signal-to-noise problem worse all the time. While CASBs can bring a layer of intelligence and control to cloud security data. It’s also easy for this to add to the problem by becoming yet another security tool to license, learn, and tune.
Make ‘Ground Truth’ an Element of Your Cloud Security Strategy
It’s easy to assume that all cloud security happens in the cloud. But the reality is that most cloud usage originates from traditional endpoints. Options like local synchronization of Google Drive files and Google apps offline mode blur the lines between the cloud and endpoints even further.
Getting direct knowledge of endpoint activity and integrating it with what’s going on in the cloud is extremely beneficial, and should be part of your G Suite security best practices. For example, if your G Suite Security Center reports malware detection, you can look for signs of endpoint infection to see how severe the situation is. You can also find useful elements of “ground truth” by looking at logs from your security information and event management (SIEM) tools, if you have a SIEM.
Most all larger organizations use endpoint security products and many have deployed SIEMs, so this information is already available in most cases. The problem is that the G Suite Security admin console has limited visibility into what is happening on your endpoints and in the data center. The same is true for most CASB platforms. And if you’re an SMB without an expensive SIEM or CASB, the problems can be compounded.
By contrast, the ActiveEye platform and SOC-as-a-Service team can see the big picture at all times. Delta Risk experts can view and analyze information from G Suite and other cloud services alongside your endpoint security and SIEM information. These different data sources are combined in useful ways to help prioritize what to respond to first, or, if you don’t have in-house staff to handle the issues, have Delta risk act on them instead.
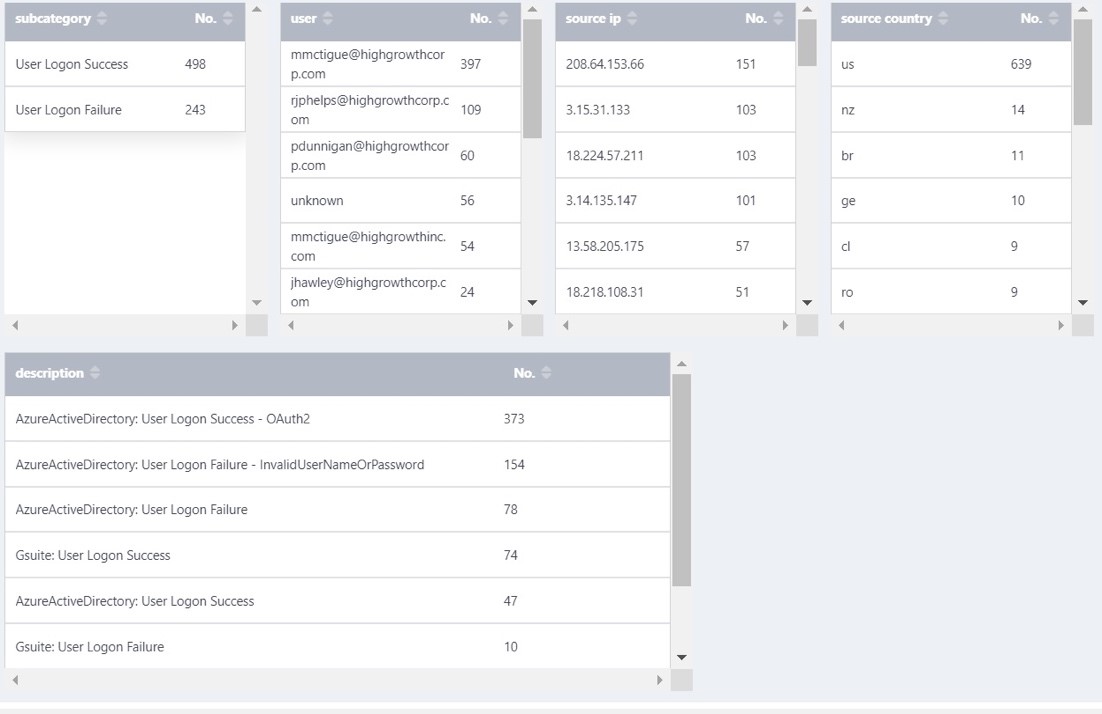
For example, if you happen to have a mix of Microsoft authentication and applications and G Suite, you will automatically have a combined view like the one below showing the login failure rate, login locations, source countries, and authentication source (e.g., Microsoft, G Suite, Okta, etc.).
Assume Your Policies Aren’t Perfect
G Suite has a rich collection of security settings, so it’s tempting to take a “set it and forget it” approach. But even with basics like two-factor authentication and strong third-party app and sharing permissions, policies are rarely perfect. It’s important to have a continuous feedback loop that links security monitoring with policy management and G Suite security best practices.
ActiveEye provides a rich set of extras beyond what is already built into Google Cloud Platform (GCP) and G Suite. ActiveEye will show you ways to make your GCP environment more secure as well as send alerts based upon user activity.
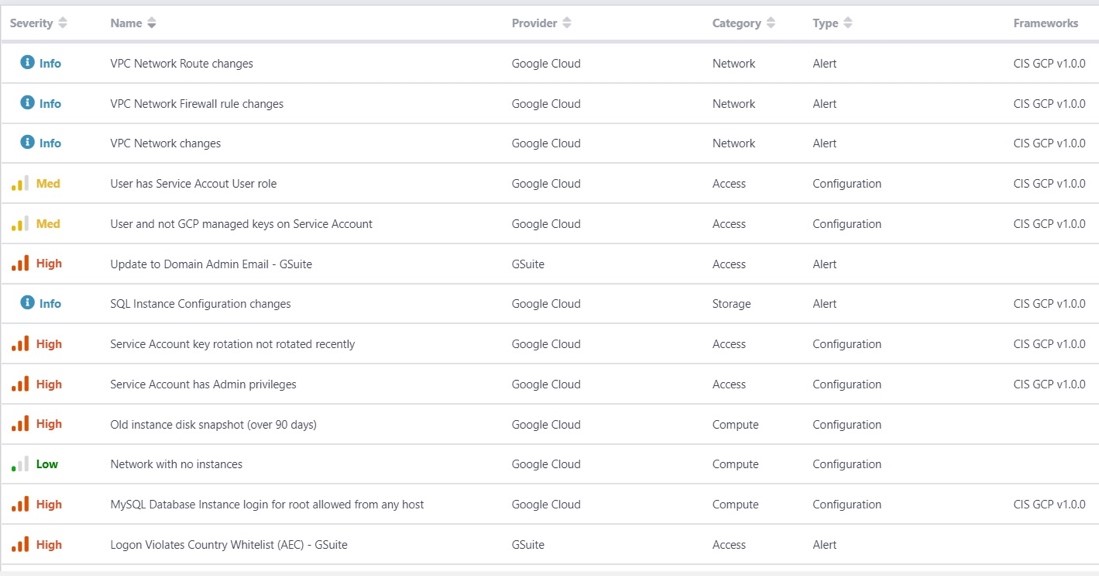
Investigating incidents can reveal new ways to protect users’ data with better policies. For example, ActiveEye uses techniques that can detect misuse of user accounts, team drives, and file sharing. Just as importantly, it can also generate policy recommendations for blocking similar behavior in the future. Expert human analysis under a SOC-as-a-service model makes it easier to be proactive and create new policies, too.
Make Compliance a Way of Life
If you’re considering a move to G Suite, compliance concerns are often a major obstacle. Expanding the scope of compliance audits to include cloud infrastructure under another company’s control is a valid concern. The best way to overcome this is to make compliance validation an ongoing effort.
Google adheres to security best practices and has achieved a number of key certifications for its infrastructure. It also makes a variety of tools available to G Suite customers to make their own compliance efforts easier. The challenge is knowing when and how to apply these tools most effectively.
This is another area where security insights from ActiveEye are helpful. ActiveEye’s integrated compliance reports map your G Suite usage to both your organizational security standards and industry compliance requirements. You can even map reports to general-purpose frameworks like the Center for Internet Security (CIS) benchmarks. This turns compliance into a way of life rather than a series of intimidating point-in-time events.
Summary
Protecting G Suite and other cloud services requires a different set of expertise and tools than traditional on-premises security or SOCs offer. But there are a number of simple steps and G Suite security best practices you can follow to improve your overall security and compliance posture.
If you already have your own SOC, you can implement these measures through an incremental investment in in-house resources or invest in expensive third-party security tools like CASB platforms, or consider adding support via SOC-as-a-Service. If you don’t have a SOC, or your current managed security services provider (MSSP) doesn’t offer cloud security services, a SOC-as-a-Service solution can provide the monitoring and support you need for G Suite and other cloud platforms.
Engaging a SOC-as-a-service partner – whether as a co-managed or fully-managed option – can make it much faster, more effective, and more economical to protect your G Suite environment, as well as your network and endpoint environment. In addition to being more cost-effective, it can ultimately keep your employees, clients, and data safer.
