In today’s post, the first of a two-part series, we’ll discuss what defines a modern SOC-as-a-Service solution, also known as outsourced or co-managed security operations center (SOC). Whether it’s to supplement experience of in-house security teams, optimize detection and response efforts, or a combination of these, SOC-as-a-Service can provide a lot of advantages that traditional outsourced security solutions can’t.
Let’s explore what SOC-as-a-Service is, what capabilities to look for in a provider, questions to ask if you’re evaluating solutions, and how Delta Risk’s ActiveEye platform addresses these needs.
What Is SOC-as-a-Service?
The term SOC-as-a-Service is frequently used as a synonym for managed security services. In our view, SOC-as-a-Service includes more features than traditional managed security service providers (MSSPs) have historically offered, though.
SOC-as-a-Service must include more than just managing alerts or outsourcing your security operations. It needs to include a fully managed, co-managed, or hybrid option, depending on your needs. It should include detection, certainly, along with automated responses for alerts based on machine learning. It should also include 24×7 “eyes on” expertise and support from trained security professionals who can address threats and situations that fall outside the realm of automated detection and response.
At a glance, a modern SOC-as-a-Service should also offer:
- API integration with major cloud platforms to gather in-depth information about how they are being used;
- Integration with endpoint and network security to show activity from them;
- A technology layer that can analyze this information and show it to you in meaningful and relevant ways;
- A team of security engineers who can perform real-time detection and incident response on a 24×7 basis via a managed SOC;
- Access to – and integration with – the latest external threat intelligence; and
- Expertise and tools to help you address security and compliance needs with effective policies.
Greater Visibility
Developers can move quickly and innovate with cloud platforms like Amazon Web Services (AWS) and Microsoft Azure. But security teams don’t always have the visibility they need to see what’s happening and respond quickly if developers accidentally create new cloud-based risks.
A modern SOC-as-a-Service solution integrates directly with native AWS and Azure security APIs to collect detailed information about how your cloud infrastructure is being used and who’s using it.
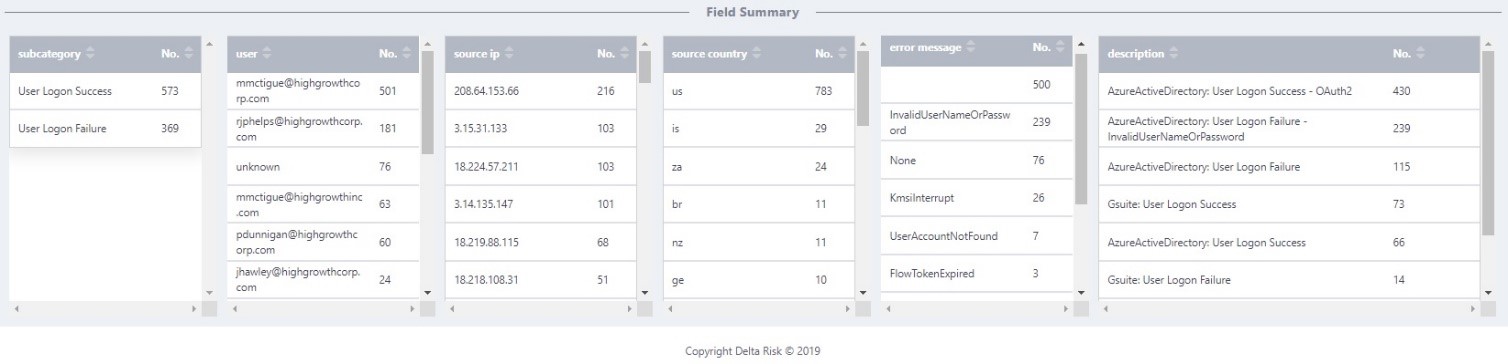
For example, Delta Risk’s ActiveEye platform is the “brain” of our SOC-as-a-Service model. ActiveEye gives you an easy way to see the expected and unexpected. In the screenshot below, we see the expected threat activity of failed logons from Asia and Russia, but also a successful logon in Asia. This could be a compromised credential or simply a legitimate login by an employee on travel.
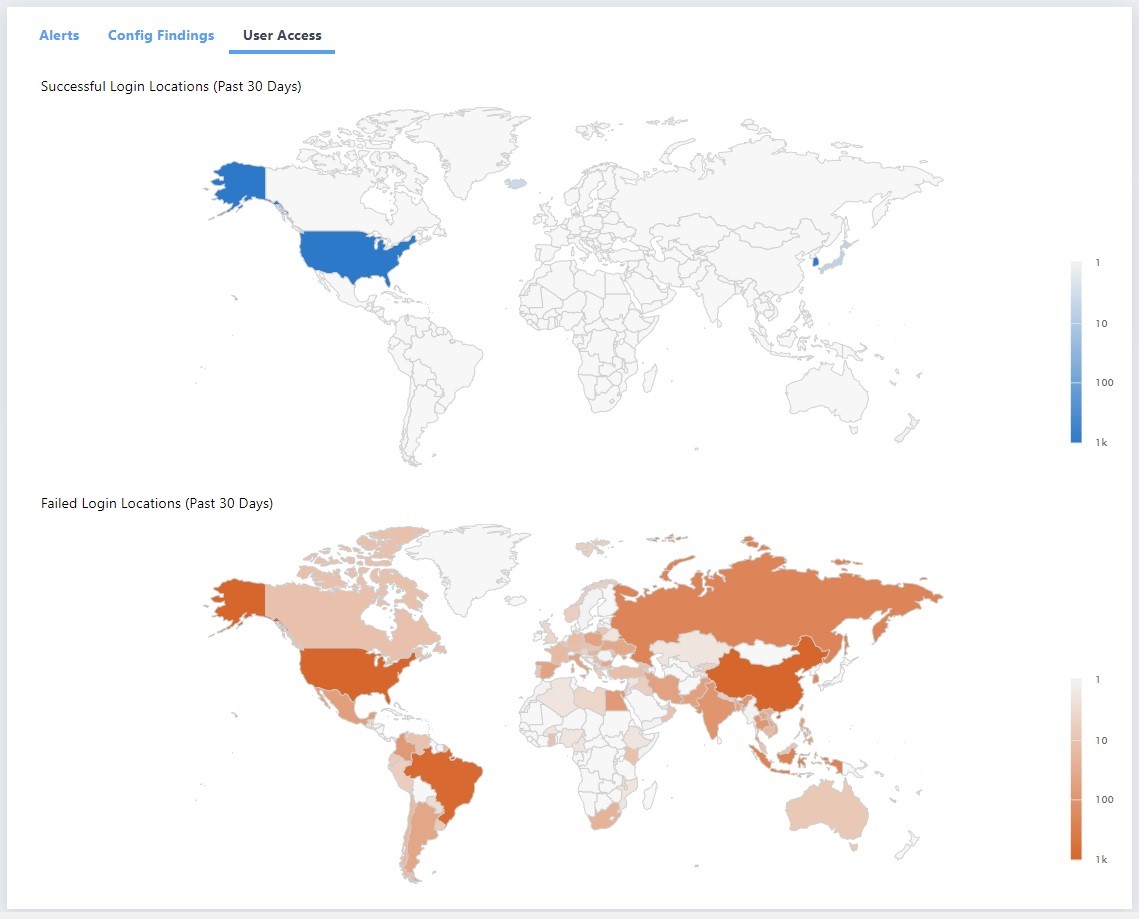
You could investigate the specific occurrence and also look broadly across all of the authentications in your various platforms and services to detect any anomalies, all without having to build a SOC.
Security Policy Guidance
In addition to showing your team what is happening in your cloud environment, you also need actionable guidance and advice for what to do when cyber threats are detected. Look for a solution that gives you a clear road map for improving policies over time to better deal with cyber security challenges.
Questions to consider:
- How are policies defined by the SOC-as-a-Service provider?
- How are they updated? Are they done manually or automatically?
- How easy is it to monitor security recommendations? How easy is it to implement them?
- Do you have visibility into seeing what the vendor’s SOC team does?
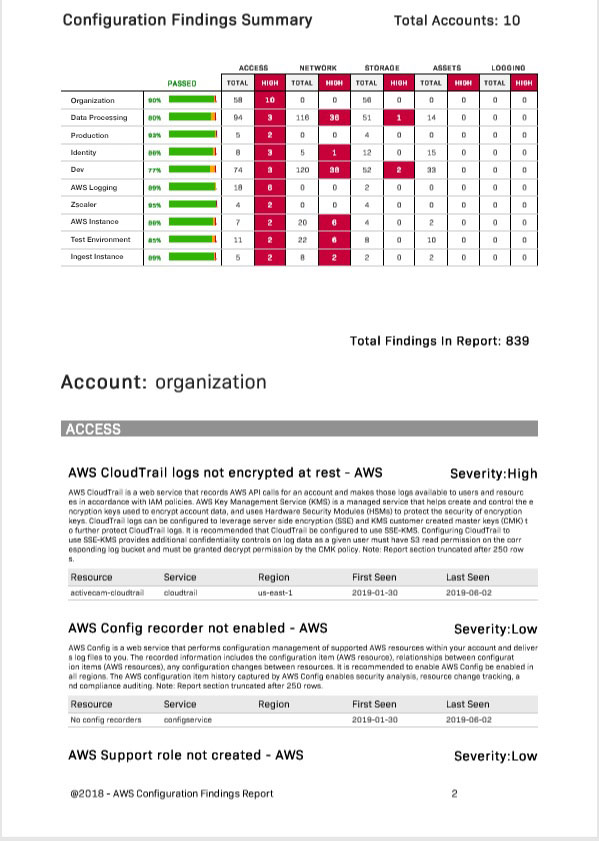
For example, ActiveEye provides a high-level view of whether your cloud environments are set up in accordance with best practices.
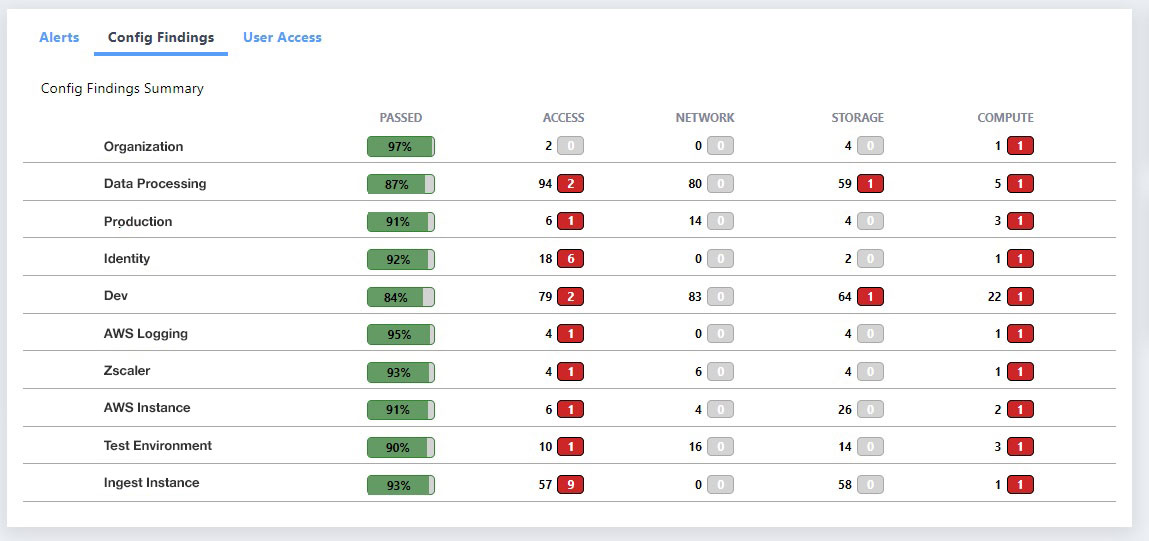
These best practices can be related to the system configurations or user activity, or other actions for which you may want to have alarms triggered.
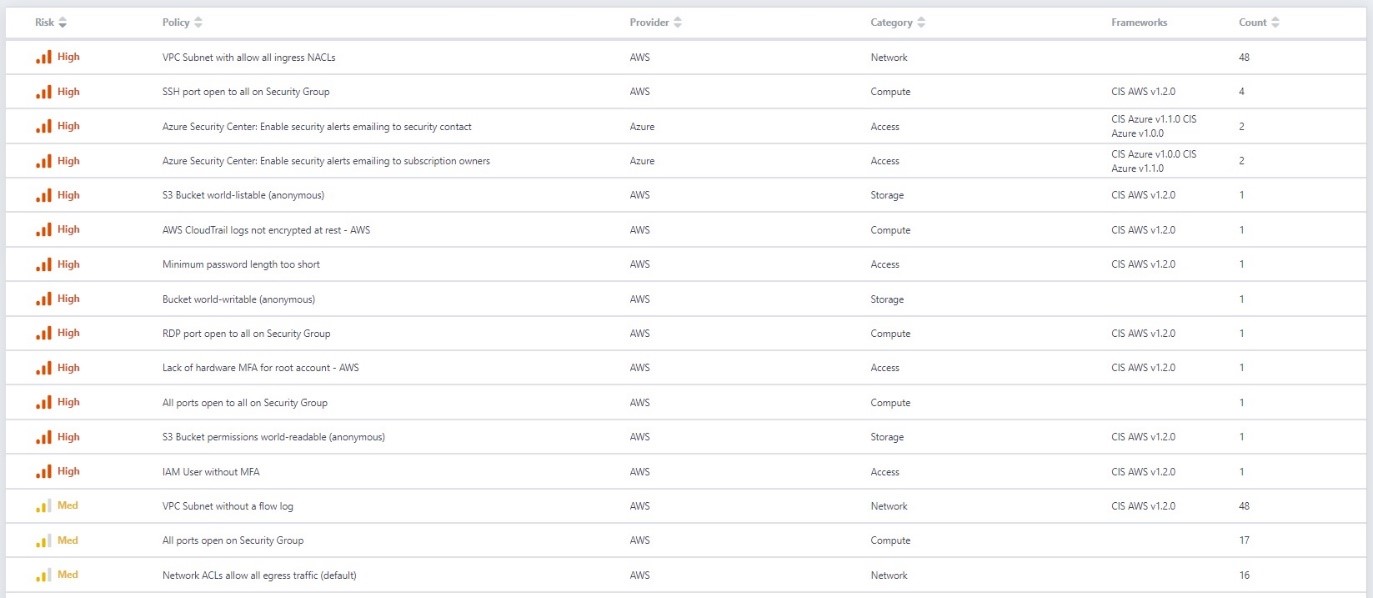
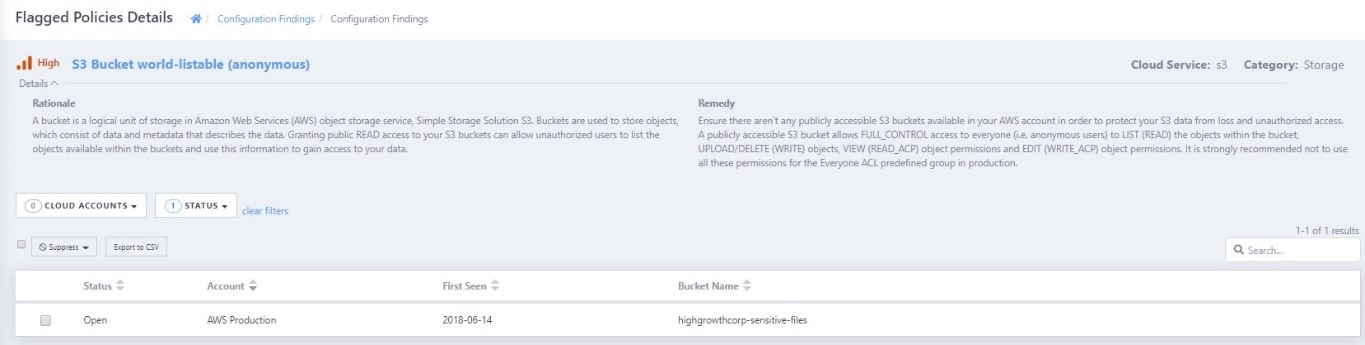
Whether for the SOC analyst or a manager monitoring their SOC services, ActiveEye provides details of why a configuration item or best practice is important and how to remediate a misconfiguration or alarm.
Active 24×7 Monitoring
Most basic security events – like password changes, failed logons, or failed accesses related to information systems, or administrative privilege usage – don’t require an immediate response, if any, under usual circumstances. There can easily be hundreds of thousands or even millions of events, even for a mid-size company. But this makes it easy for critical incidents to get lost in the noise.
One of the best ways to address this is to apply machine learning to baseline expected behavior, coupled with human review of high severity findings. This can help detect anomalies faster and more accurately than having someone going through log files.
ActiveEye uses machine learning to get smarter over time about your environment. For instance, when it detects high severity incidents in cloud platforms, our dedicated security experts respond accordingly and flag them for investigation.
This ensures that the most critical issues are escalated to your security team or ours, depending on your preferences, for a timely response. It’s easy to see all this activity from your ActiveEye account, via alerts to tools like Microsoft Teams or Slack, or both.
Compliance
One of the most complex aspects of adopting Infrastructure-as-a-Service (IaaS) platforms like AWS and Azure is making sure you meet compliance requirements. Look for a solution that includes integrated compliance reports to help your team achieve compliance and provide the necessary validation to any external auditors.
Questions to consider:
- Are compliance requirements fully integrated into the vendor’s SOC-as-a-Service solution?
- How often are they updated, and how?
- Does the vendor offer 24×7 expertise from analysts that have compliance experience in your industry?
For instance, Active Eye has built-in reports to help you keep your systems in line with best practices as well as compliance frameworks. The report below shows compliance of an AWS environment with the CIS AWS 1.2.0 1.12 security guidelines.
Summary
Although some analysts and security professionals dismiss SOC-as-a-Service as yet another buzzword or vendor hype, we think it’s a useful way to describe premium managed security services. We often use the terms interchangeably. But it’s important to consider how changing technologies and security requirements affect what you should expect from a managed security service provider.
An effective SOC-as-a-Service offering must have the flexibility to support both fully outsourced and co-managed approaches. It should also apply advanced machine learning and data analysis techniques to make security analysts more efficient and effective. And lastly, it’s essential that SOC-as-a-Service providers have expertise and technology integrations with both traditional on-premises security products and leading cloud platforms.
In our next blog post, we’ll expand on that final point with a focused look at how SOC-as-a-Service can improve your AWS and Azure security.