When you enlist a hunt team to run compromise assessments, it’s important to determine which solutions and processes they’re using to actively hunt down threats. After all, compromise assessments (time-bound or more focused projects) are proactive efforts to detect persistent threats that have evaded existing security controls. You must adopt the mindset that your existing controls have already failed – which means using defensive or detection solutions really defeats the purpose of hunt.
Let’s take a closer look at the difference between threat hunting and real-time defensive solutions. Detection solutions, like real-time monitoring, focus more on capturing low false positive (FP) alerting. The goal of real-time monitoring is to keep these false positives low and to sound the alarm for actual security incidents.
On the flip side, threat hunting tools are geared to pull and mine as much data as possible. False positives aren’t as big of a concern. If anything, if there are a higher number of false positives that occur in the subset of data hunt teams are examining over the course of a few months, these patterns could form the basis of a lead.
Ultimately, threat hunting and detection are not the same thing. This can be a big misconception. When it comes to threat hunting, you are not waiting for alarms to go off, which is what real-time detection is all about. You’re inviting low false negatives (FN). The diagram below (a standard model of machine learning) represents where the focus of threat hunting data should fall – between the good (low FP) and bad (low NF).
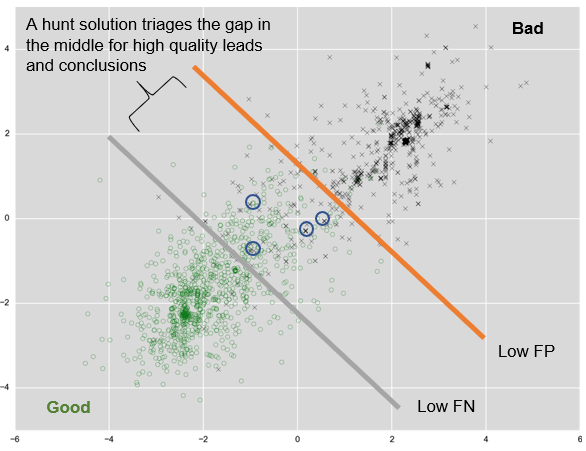
Anomalies, outliers, and suspicious activities are leads that need to be scored. Threat hunters should have enough data to conduct their own investigation and analysis without having to rely on tools that flag potential incidents. The goal of any threat hunter is to triage those leads to find threats they couldn’t find before.
What are some of the other tools and techniques you should ensure your hunt teams are using to successfully hunt down malicious threats? In the webinar, “Threat Hunting Versus Compromise Assessments: What’s the Difference?” Infocyte Founder and Chief Product Officer Chris Gerritz and I discuss various hunt methodologies that hunt teams can employ. View it on-demand.
