In part one of our blog on network segmentation and security, we talked about how network segmentation can improve security and help you protect critical assets. We also covered two segments of network segmentation design as part of layered security.
In part two, we’ll discuss two additional segments and how to go about protecting them with network segmentation to improve security.
The General Support Segment
Next, let’s look at the traditional Server Farm as shown in Figure 3.

Note: The segmentation was done using a firewall instead of a router. The reason is that firewalls provide better control and logging than routers. Additionally, if the selected firewall is a NexGen firewall, they’ll have additional features available. NexGen firewalls include intrusion detection system (IDS) functions, antivirus (AV) functions, and threat monitoring, and some include SSL intercept capabilities. By combining IDS, threat monitoring and firewall logs into a single device, alerts on server events are semi-centralized, the server segments are logically separated from all other segments, and an important layer of security is added.
The General Support segment is an area for servers that provides services to most users. This can include home folders, Active Directory (AD), Domain Name System (DNS), Dynamic Host Configuration Protocol (DHCP), email, and internal web services. These services seldom need firewall rules to block internal network segments since all users and systems need the services to communicate on the network. Commonly these services are monitored or prevented from leaving the internal network. The key here is to limit authenticated access to General Support servers to relevant admins and user services only. Unauthorized ports and protocols are stopped prior to entering the segment and alerted.
The HVA segments here follow the same logic as the HVA segments in the DMZ. If HVA services exist, separating them even from other services allows strong monitoring and protection. The application segment is servers that host web front ends or stand-alone applications that are independent. These servers may have limited users or provide a specific capability but are not critical in the sense of an HVA.
Since users shouldn’t directly access databases, you should also segment those. Databases are typically accessed by web front-end servers or client applications on workstations. Database host large amounts of company data and are subject to common attacks, like SQL injections. By placing a security segment around the database, the attack surface is reduced, and alerting is timelier.
The segmentation discussed for servers defines areas of control against pivoting, builds alert grouping by types of data, allows the creation of focused alerts for continuous monitoring, and helps define the level of criticality of services internal to the company. Each segment becomes a layer of security within the network targeted at protecting server assets.
The Management Segment
The final area to segments is the management segment from Figure 1. This segment has a higher risk due to two factors. First, since the users in this area are considered privileged users, that means their accounts (privileged accounts) live in this section, too. Those accounts can reach all other parts of the network and can affect all systems on the network. Second, many security tools live in the management segment.
As most of us know, management tools are a prime target since they hold all your vulnerabilities. Security tools are often not monitored since the tools are the ones doing the monitoring. Basically, this area has the most capable user information and confidential information about your security posture. Protecting this area from both intentional and unintentional actions is required, as shown in Figure 4.
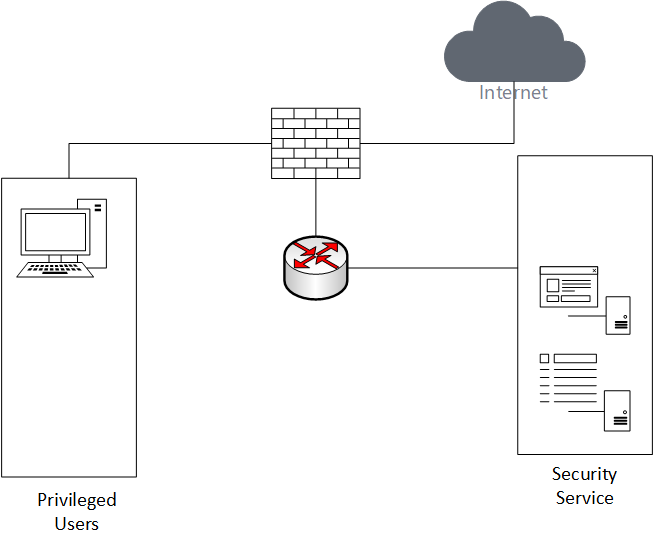
Here’s what you can do. Divide the management network into two segments: Users and services. The privileged users’ segment is a place where your greatest trust and greatest risk co-exist. These users require the most access and are responsible for the operation of all services. This segment can also provide a malicious actor access to all other segments. Knowing what’s happening in this segment is critical to the security of your network.
You should also reduce the attack surface by removing security services to a separate segment. Increasing the criticality of alerts from this segment is also a good idea. Remember, this won’t just mitigate an insider threat. It also limits malicious actors and minimizes pivoting into the network.
Because the nature of security tools means they need full access to validate systems, a firewall can often affect the functionality of the tool, unless all tools have remote sensors. A simple ACL with logging will monitor access to the tools and isolate users’ access. The main idea is to isolate these services from all other target areas without negatively impacting the tool’s capabilities. As for justification, consider your network vulnerability scanner. This device identifies existing vulnerabilities within your network, but it doesn’t scan itself. By using the segmentation to reduce access to the scanner, you reduce the likelihood of unauthorized access to the information contained in the scanner.
Once a complete network segmentation design is in place, services are protected from each other, layers of security are implemented at multiple points within the network, and monitoring can occur prior to the endpoint. A structure that supports mitigating the risk of privilege escalation, pivoting, and insider threat is available for use.
Summary
To summarize, network segmentation is the foundation within the design to support performance, layered security, and continuous monitoring. By evaluating your network by business need and liability, you can create and implement a segmentation design to support your operation and protect your assets.
