What is network segmentation? In simple terms, it refers to using subnets to separate sections of a network. There are several use cases for network segmentation: improved performance, better security, compliance, or even continuous monitoring. Regardless of the reason, the goal is to create separate subnets, or segments, for known network traffic.
In this blog, we’ll talk about how network segmentation can improve security and help you protect critical assets. We’ll also look at network segmentation design as an aspect of layered security. This includes using segmentation to enable continuous monitoring, as recommended by the Department of Homeland Security (DHS) Cybersecurity & Infrastructure Security Agency (CISA) and the National Institute of Standards and Technology (NIST).
The Basics: Network Topology
Let’s start with a basic network topology, as shown in Figure 1 below. Imagine each switch as defining a virtual local area network (VLAN). There’s some separation at Layer 2 of the Open Systems Interconnection (OSI) model on each switch, but the subnet separations all funnel back up to a Layer 3 device. Put simply, this design is based on the old “router on a stick” design. This is a “worst-case“ design but it allows us to explore the advantages of network segmentation. The design includes a public-facing Demilitarized Zone (DMZ), separation for all servers, and a separate network management subnet that includes privileged users and non-privileged users.
The hardware used to support network segmentation typically includes routers, Layer 3 switches (specialized hardware devices), and/or firewalls. The layers security will use the segments to place packet captures, intrusion Detection and protection (IDS/IPS) sensors, SSL intercept and/or proxy services. Continuous monitoring uses the logs from all the above plus a systemic alert structure that monitors them. The goal is performance, security, and monitoring.
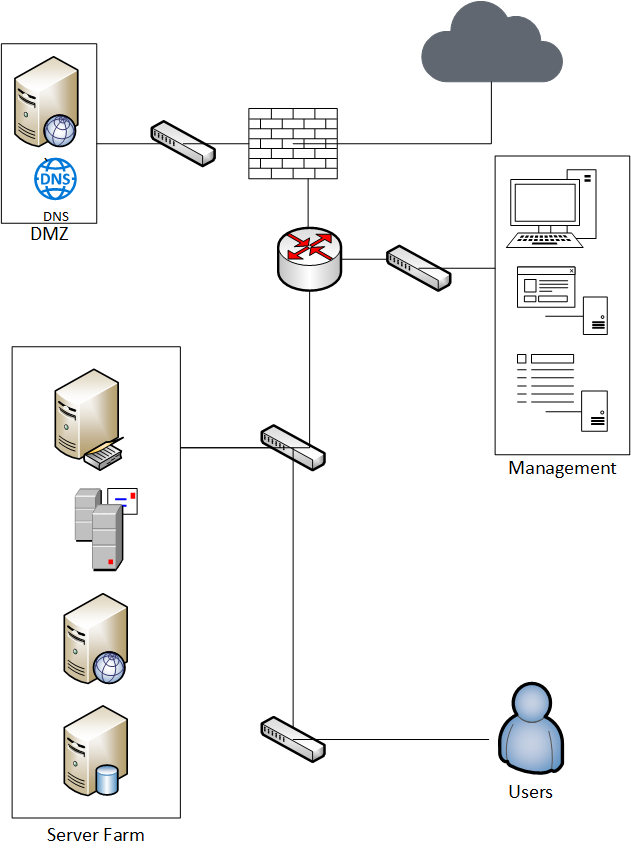
The network shown in Figure 1 makes the router the key director of all traffic on the network. It works on a first in-first out concept, so it doesn’t prioritize performance of key services. Also, traffic from various areas of the network can broadcast to other areas, so any IDS/IPS must allow the traffic to avoid false-positive alerts. Performance is impacted by forcing the router to handle all routing and forcing all traffic into the single router interface.
The simple fix, from a performance perspective, is to add some Layer 3 switches or additional routers to distribute the load. Most Layer 3 devices also include the ability to apply Access Control Lists (ACL) which also adds a limited security point and can separate traffic into types for the IDS/IPS alerting. However, we have yet to investigate the types of traffic on our network or optimize the performance of important network traffic.
The Value of Network Segmentation
Let’s use the DMZ as our first example to better explore the value of network segmentation, as shown in Figure 2.
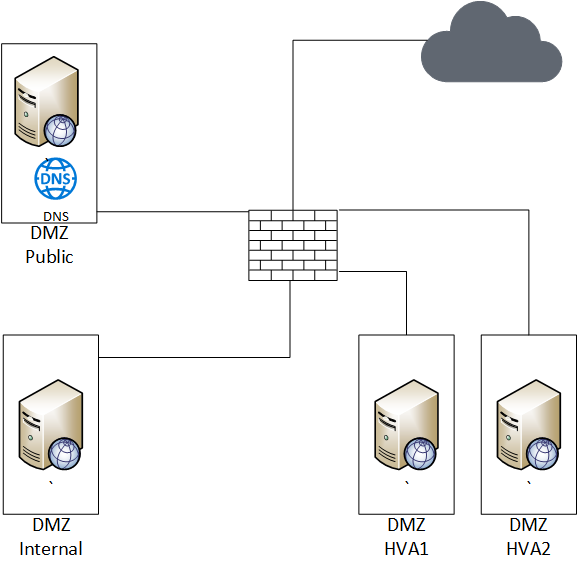
This change does not directly affect the performance of devices within the DMZ, so these segmentations add layers of security. Let’s look at the reasons for these segments. A DMZ’s normal usage is to provide access from the Internet to a limited number of resources. However, those resources can be split into two groups: a resource that’s contained in the DMZ and a resource that depends on internal resources.
A common example of the first resource can be an external DNS service or a public web page. An example of the second could be a web front end application that allows access to an internal database. The advantages of separating the two types are tighter controls on allowed traffic, improved ability to build custom alerts specific to each segment, and minimizing the risk from getting access to internal systems.
The third separation is built based on the DHS and NIST defined High-Value Asset (HVA). Although HVAs may not exist in the DMZ, separating them is a best practice if they do. Because HVAs are so important, it’s crucial that they’re protected from other trusted resources so they aren’t impacted by accidental or intentional events within the network.
Although this may seem like it would only apply to the Federal government, any industry or company can have HVAs. This could include everything from confidential information to systems that are used to protect consumers and customers. For example, consider the systems used to recall cars, drugs, and food. If no one issued recall alerts, would you feel safe? Probably not, because of the potential loss of human life and the safety risks to yourself and others (as well as financial risks to companies from lawsuits) – which is why these are also considered HVAs.
As you look at business continuity and disaster recovery plans, consider the cyber security assets that have the most impact on legal liability, safety, and intellectual property. If you have these systems in your DMZ, it’s best to isolate them.
Segmenting your network can enable tighter controls and better alerting within the DMZ. Both can reduce risk and improve response time.
In part two of our blog, we’ll discuss two additional segments and how to go about protecting them with network segmentation to improve security.
