Delta Risk’s Stephanie Ewing-Ottmers, Senior Associate, and Constantine Pavlis, Cyber Intrusion Analyst, made return appearances to Black Hat and DEF CON last week. In their own words, here’s what they experienced at the 2017 conferences.
DEF CON 25
In the words of Constantine Pavlis
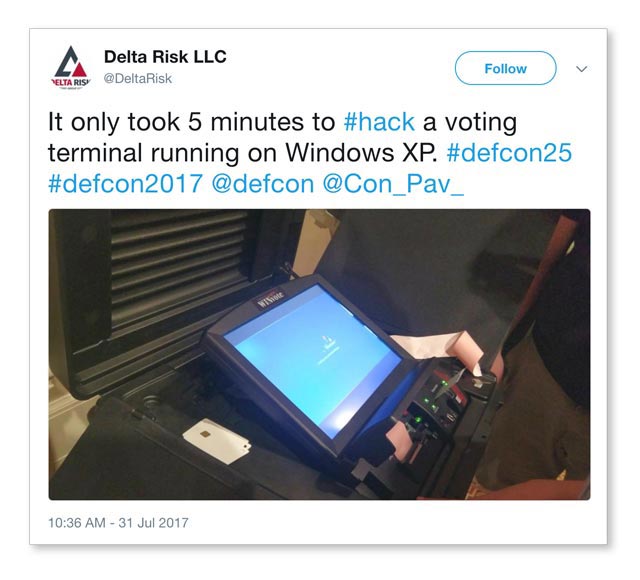
From jailbreaking Apple watches to hacking the cloud to exploiting wireless radio devices, DEFCON 25 had something for everyone. More than 30,000 attendees had the chance to hack over 30 electric pollbooks and voting machines at the Voting Machine Hacker Village. On average, it took 90 minutes to find vulnerabilities in these machines. In the case of one voting terminal that ran on Windows XP, it only took five minutes to exploit.
Although this year’s twenty-fifth conference didn’t have a singular theme like last year (“rise of the machines”), there were specific topics that remained popular. For instance, exploitation of personal fitness tracking devices is still a concern. The is a perfect example of security implementation and protocols needing to keep up at the rate of technology advancement and consumer adoption.
Here are some of the other talking points that piqued my interest.
Moving to the Cloud Isn’t a Security Workaround
You may have heard this before: “I can’t afford to implement all the security measures, so I’m moving to the cloud!” Moving to the cloud or employing hosted cloud services presents new challenges. Even if you understand your network, do you understand what’s happening to your data and who can access it beyond your network boundaries?
In the “Hacking the Cloud” presentation, speakers covered bidirectional attacks from the internal network to the cloud and from the cloud to the internal network. They also focused on how to take domain access and leverage internal access as a ticket to a target’s cloud deployments.
Exploiting Common Remote Administration Tools (RATs)
Most applicable to my line of work was a talk on the not-so-surprising exploitability of common remote administration tools (RATs) used by various adversaries to effectively turn the table on attackers. The speaker, who only went by the name “Professor Plum” and title “Hacker,” found some straight-forward ways to exploit the server-side components of various RATs, including PlugX and Poison Ivy. He effectively took control of the attackers’ machine.
This discussion reminded me of the recently updated Active Cyber Defense Certainty Act (ACDC) legislation, which would lawfully exempt victims from hacking laws when they identify their assailant, cut off attacks, or retrieve stolen files. While I’m personally not a proponent of the “hack back” strategy, many of the techniques described in this talk could make for interesting times ahead if they become lawful.
The Software Engineering Institute (SEI) and Carnegie Mellon are working on modeling the computer network operation ecosystem to account for both adversaries and defenders. While academic in nature, it’s a novel approach to network architecture that blends traditional threat intelligence with technical analysis, offering a better understanding of nonlinear behavior of interactive systems through flows and feedback loops over time.
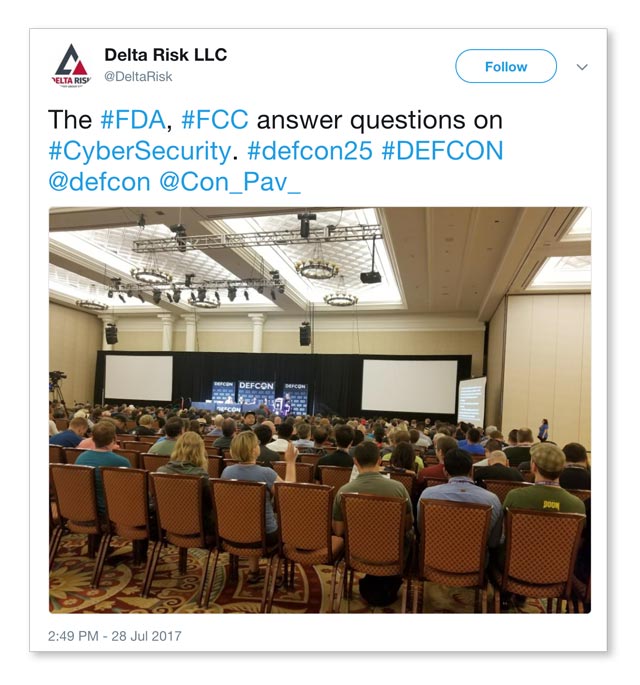
Meet the Feds
“Meet the Feds” was one of the livelier discussions I attended. The panel was made up of representatives from the Federal Drug Administration (FDA), Department of Justice (DOJ), Center for Strategic and International Studies (CSIS), and a “cranky” law professor. They focused on how the U.S. government can bring the hacker community closer to the larger security community in a push to improve security posture.
Audience participation truly made this panel discussion highly engaging and interesting. The group directed general and focused questions around motives, due diligence, bureaucracy, and perceived ineptitude over the loss of loss of unreasonable amounts of data, including personal identifiable information (PII). On many occasions, the focused questions elicited long and loud rounds of applause.
Summary
All in all, DEF CON 25 provided some thought-provoking theories and hacking methods that are important for the security community at large. There were many talks I was unable to attend due to long lines, but I look forward to reviewing DEFCON’s public release of notes.
Black Hat 2017

(From top left to bottom right: Alex Stamos keynote, the band KISS, CrowdStrike presentation, AlienVault booth)
In the words of Stephanie Ewing-Ottmers
So many sessions, so little time. Like DEF CON, Black Hat also celebrated a milestone anniversary, with this being the twentieth year this has been held. Among the topics that dominated this year’s conference were AI machine learning and data analytics, but there wasn’t a central theme.
Black Hat kicked off with an opening keynote from Alex Stamos, CSO for Facebook. He asked the security professionals in attendance to re-examine traditional security approaches to keep up with modern technology advancements.
Stamos implored the crowd that there is a greater need for hackers to focus on defense instead of the thrill of unlocking new vulnerabilities. He also discussed having more empathy for end users. Security experts need to put themselves in the shoes of the people they are trying to protect. In addition, it’s important for hackers and the security community to understand the point of view of law enforcement and government officials.
There were some compelling sponsored sessions and workshops that stood out more than others. In particular, Imperva presented the highlights of their report, “Beyond Takeover—Stories From a Hacked Account”, providing insight into the behaviors and cycle times of an attack.
Of course, there were several sessions dedicated to ransomware. Is ransomware here to stay? Most definitely. In one presentation, CrowdStrike explored the many factors for ransomware’s staying power, including an infinite target set, high success rate, and immediate profitability. With the rise in ransomware and other threats, incident response plans and backup processes need to be tested and verified.
Summary
This year’s Black Hat event presented a mix of well-rounded content to keep the large crowd of info sec professionals from all levels and backgrounds engaged over six days. You simply can’t find an event like Black Hat that offers a showcase of so many unique perspectives and demonstrations of what’s trending in information security.
