In our previous blog, “New York Cyber Security Regulations: Are You Ready to Implement 23 NYCRR 500?” we provided a brief overview of the New York Cyber Security Regulation (23 NYCRR 500), including how to identify if your company is a covered entity under the New York Department of Financial Services (NYDFS). It also outlined the requirements of the regulation, who is exempt from certain aspects of the law, and which controls need to be prioritized and completed before the end of August.
One of the key things to note about 23 NYCRR 500 is that it overlaps with the guidance and requirements for entities who are already in compliance with the GLBA or have met the FFIEC standards outlined in their IT Handbook. Most financial organizations that are considered covered entities under 23 NYCRR 500 will have already addressed some requirements outlined in GLBA or FFIEC IT Handbook. However, it is important to know that while there is overlap in the requirements, there are also some substantial differences needing to be addressed to comply with 23 NYCRR 500. Understanding these differences will help you leverage existing investments in security and develop a plan of action to address any gaps.
Comparing Cyber Security Requirements for GLBA, FFIEC, and 23 NYCRR 500
GLBA
Passed into law in 1999, the Gramm-Leach-Bliley Act (GLBA) is an incredibly large piece of legislation that outlines everything from requirements to ensure the fair treatment of workers by financial firms, to the removal of Glass-Steagall, to establishing administrative, technical and physical safeguards to protect customer records and information. The guidelines are only meant to be applied to “non-public” customer information. They are written in general terms to accommodate the wide range of business models among financial institutions. GLBA was one of the first regulations to introduce personal data security requirements and is therefore very vague. It allows for organizations to assess their own risk and identify their own controls to mitigate any risk found. With such flexible requirements, companies can implement safeguards that are appropriate to their own circumstances. Therefore, the success of the information security program largely depends on the employees who implement it.
FFIEC
The Federal Financial Institutions Examination Council (FFIEC) is comprised of five banking regulators: the Federal Reserve Board of Governors (FRB), the Federal Deposit Insurance Corporation (FDIC), the National Credit Union Administration (NCUA), the Office of the Comptroller of the Currency (OCC), and the Consumer Financial Protection Bureau (CFPB). As the “umbrella” organization that was formed to unify standards, principles, and reporting, it has provided financial institutions with guidance and recommendations on addressing security risks. Over the last few years, the FFIEC has focused on cyber security initiatives that include developing and provisioning its Cyber Security Assessment Tool, enhancing its capabilities to conduct incident analysis, and updating its IT Examination Handbook to include cyber security best practices. While the Examination Handbook provides an understanding of what auditors and examiners will be looking for in a security program, financial firms still have the flexibility to implement what is deemed necessary to protect the organization from cyber threats. It is safe to say that the FFIEC has created a handbook that is best used for guidance on how to meet compliance with a “baseline” set of practices rather than prescribing specific controls, policies, technologies.
23 NYCRR 500
The New York Cyber Security Regulation by the NYDFS went into full effect on March 1, 2017. It is meant to address risk to all regulated entities of NYDFS by outlining a minimum standard while not being “overly” prescriptive. This regulation is aimed at not only protecting customer data, but fortifying information systems that financial organizations use to handle sensitive information. Since most financial organizations are already required to meet guidelines outlined in the FFIEC, SOX, and the GLBA, the New York Cyber Security Regulation is more prescriptive in nature. It requires institutions to implement specific policies, procedures, and technologies to comply with the regulation.
Overlap Between the Regulations
At a high level, there is extensive overlap in the requirements outlined in the 23 NYCRR 500 regulation and existing requirements. Most of the NYDFS’ requirements are at least, in part, already addressed by GLBA or the FFIEC IT Examination Handbook. However, there is also more detail outlined in the NYDFS requirements that dive deeper into sub-requirements the NYDFS will look for from covered entities. It’s important to identify the commonalities and outliers among the requirements so you can adjust your programs accordingly. This will prevent unnecessary work and increase your ability to be compliant by February 15, 2018. The table below shows the overlap in the security requirements outlined in the three approaches:
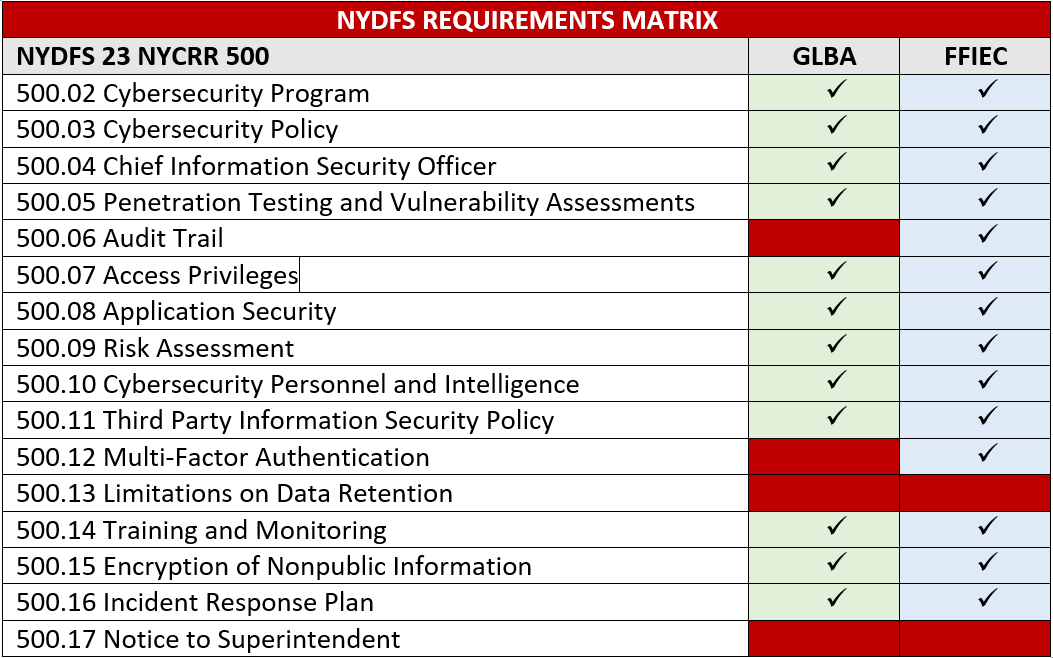
If your organization has already met the requirements above via GLBA or FFIEC, then you’re halfway there. If your institution has not had to abide by the regulations or guidelines above, you may have quite a bit of work to do.
Differences Between the Regulations
As outlined above, there are obvious differences between 23 NYCRR 500 and the GLBA. When comparing 23 NYCRR 500 to the GLBA, the major differences are in audit trail practices, data storage, and multi-factor authentication implementation. These disparities are somewhat expected, as the IT landscape has matured considerably since the GLBA regulation was created more than a decade ago. With respect to the overlap between FFIEC’s guidance and 23 NYCRR 500, there is only one high-level difference between the two: the implementation of limitations on data retention.
At first glance, most of the controls look as if they overlap tremendously. However, there are some minute details in the NYDFS regulation which really differentiates it from the GLBA and FFIEC guidelines. This is a result of how the regulation is written and the NYDFS’ goal to implement a minimum standard amongst covered entities. This is seen in the prescriptiveness of each of the requirements that 23 NYCRR 500 outlines. Most, if not all, requirements go into detail on which policies the organization must create to support specific requirements, and what aspects should be included in policies and procedures. They also detail the frequency of ongoing monitoring and training as well as the notification timeframe.
This in-depth detail can be seen by comparing the NYDFS regulation with the GLBA and FFIEC requirements to create policies, standards, and procedures. As shown in the table below, here are some major differences between GLBA, FFIEC, and 23 NYCRR 500.
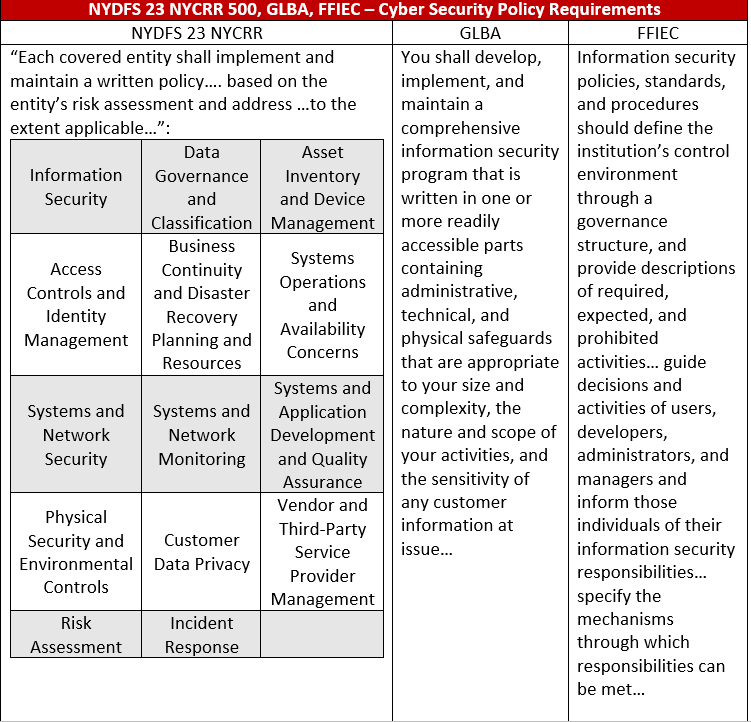
This table provides an understanding of the intentions of each rule set. It’s clear how subtle changes in language dictate an entity’s ability to use its own “discretion” to meet a requirement.
Summary
If your organization currently meets GLBA and FFIEC standards, don’t make the mistake of assuming that compliance with GLBA and FFIEC will satisfy NYDFS’ prescriptive requirements. The guidance provided in GLBA and FFIEC will touch on many sections for the regulation. However, depending on how the requirements are already addressed, it may not allow your organization to inherit controls from other frameworks and standards.
Still unsure of the steps you need to take to meet 23 NYCRR 500 requirements by the end of August deadline? Check out our infographic and contact us. We can assist to help secure your organization as a trusted advisor and service provider.
