Earlier this week we announced that Microsoft Defender ATP is now integrated with our cloud-native Security Orchestration and Automation (SOAR) platform, ActiveEye. In today’s blog, I wanted to share a bit more context about what this means from a practical perspective.
Adding support for Microsoft Defender Advanced Threat Protection (ATP) is part of our strategic approach to incorporating Microsoft security technologies. If your organization runs on Microsoft, we can provide Managed Detection and Response (MDR) through our platform. We also have a 24×7 security operations center (SOC) to evaluate alerts, set policies, and respond quickly to any critical threats or alerts.
What is Microsoft Defender ATP?
Microsoft has been upping its security game in the past year. One component worth considering if you’re a Microsoft shop is their endpoint security solution, Microsoft Defender ATP. This is a feature you can license with some of the premium Office 365 packages.
There’s no question that a modern endpoint security solution is a required investment if you want to fend off malware and ransomware from your systems, both on and off the enterprise network. Especially now, protecting remote workers and endpoint devices is more critical than ever.
Since antivirus solutions aren’t as effective as they once were, it’s really a matter of figuring out which next-gen endpoint security solution is best for your environment. With Defender ATP, Microsoft provides next-generation malware protection. In addition, it offers threat hunting capabilities for your Windows desktops and servers as well as some macOS and Linux systems.
Why Is Endpoint Detection and Response More Complex to Manage?
Like other endpoint detection and response (EDR) solutions, the Microsoft Defender ATP detection capability is strong. However, understanding all the information you get from the output requires a deep knowledge of the operating system processes. It also requires experience with the current threat landscape. Many files are going to fall in the grey area where they aren’t necessarily malware but take enough information from your systems that you really don’t want them running in your environment.
Another thing to consider is that attacks are evolving to be “file-less.” This means that they don’t require complete applications to be downloaded to user machines, which enables them to evade traditional defenses. You will need someone available to decipher these situations and make quick decisions about blacklisting the file or terminating a system process.
My point isn’t to scare you away from EDR. It’s just that unlike traditional antivirus, deploying Defender ATP or other EDR solutions requires daily attention to tune your environment. It also requires the ability to respond quickly when a malicious actor gets a foothold.
This is why we integrated Defender ATP with our ActiveEye platform. We use orchestration and automation to make it easy to eliminate false positives and investigate any alerts or issues in a matter of seconds – not hours. If programs need to be quarantined or machines isolated during an investigation, we can do it via the ActiveEye interface, or through the managed service provider (MSP) portal to your Defender ATP console.
Defender ATP: One Component Available Via Microsoft Graph Security API
The Defender ATP integration is just one component of the Microsoft Security connector. ActiveEye can also pull any other data available through the Microsoft Graph Security API, including monitoring Azure Identity Protection activity and Microsoft Cloud App Security activity. With a partnership to provide SOC-as-a-Service around all of these Microsoft solutions for attack surface reduction, more organizations stand a fighting chance against a relentless adversary.
You may have noticed that I didn’t say “Microsoft Defender ATP” connector. This is because the API we use is the Microsoft Graph Security API, which has an aggregated feed of security events from the various applications.
The simplest explanation of this process is in this graphic from a white paper on the Microsoft Graph Security API .
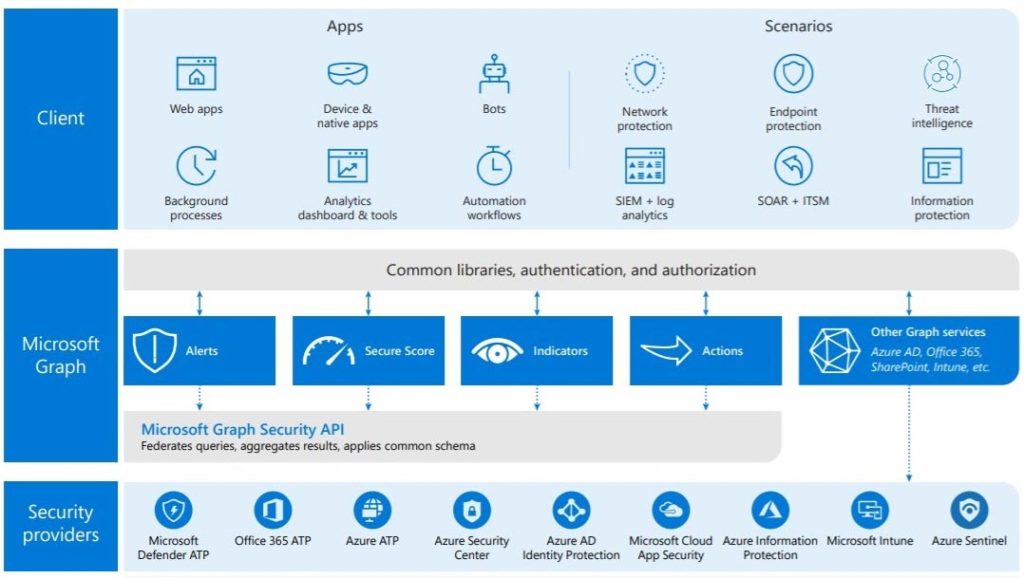
With our ActiveEye Microsoft Security connector we get the events from Defender ATP for manual and automated investigation. We also get a buffet of Microsoft security sources served from the common table of Graph Security.
If you look into Microsoft Graph Security it is easy to be a little confused, depending upon which content you read. The Microsoft Graph Security API, which sounds like it would be about security for graph, isn’t security for Microsoft Graph at all. It is actually the conduit for the security data from various Microsoft (cloud based) security products. If that wasn’t confusing enough, you may also run into something called Microsoft Intelligent Security Graph. This is an analytics and intelligence platform that uses the Microsoft Graph Security API as its data source.
Summary
Deploying a next-gen EDR solution is one of the best ways to improve your security posture and Microsoft Defender ATP provides all of the capabilities you’d expect. What it also provides, as with any EDR solution, is an overwhelming amount of data to process. Delta Risk makes it far easier to manage this. ActiveEye can be configured in under 30 minutes to get the Defender ATP data for investigation and remediation.
If you’re a Microsoft shop or Office 365 customer you may already use some of the other services that feed into Graph Security, like Office 365 ATP, Azure Identity Protection, Microsoft Cloud App Security, and Azure Security Center. The events and alerts from all of these sources can be ingested into Active Eye to catch emerging threats faster.
