We recently announced our expanded partnership with VMware Carbon Black for improved endpoint protection. Our technical integration, via our ActiveEye portal, delivers managed detection and response (MDR) capabilities that enable us to be much more responsive and go beyond basic prevention, especially when it comes to endpoint protection.
In this blog, I’ll dive deeper into what our expanded partnership means in practical terms, and how it can benefit you.
Endpoint Protection Through ActiveEye: How it Works
The Delta Risk ActiveEye platform is set up so that our security operations center (SOC) team can directly support VMware Carbon Black clients through a single portal instead of having to log into two different platforms. We also partner with a number of incident response (IR) firms, many of whom use Carbon Black to address incidents. They use Active Eye and our Carbon Black Connectors to streamline their investigative process.
By consolidating all of the endpoint detection and response (EDR) alerts through Active Eye, incident responders can spend more time focusing on actual threats instead of false positives. This frees up more time for other security activities and threat-hunting.
One of the main advantages of ActiveEye is that it’s a co-managed portal. This means that everyone involved operates from the same playbook. Both our SOC team and the client team can see the same critical information and track any activity in real-time. This makes operations much more efficient and avoids the dreaded “who’s on first?” situation.
Every client has a customized escalation process (Figure 1) that defines and documents who gets notified when a Carbon Black endpoint agent triggers an alert. Most of the time the Active Eye “Virtual Analyst” – a combination of our artificial intelligence and machine-learning capabilities – resolves alerts without interrupting the SOC analyst.
Customer Bulletins also provide directions for how to handle special situations. This feature is even more important and useful when an IR firm or SOC team needs information for multiple clients. It also helps when Carbon Black identifies a certain type of threat. In that case, the hash, domain name, or IP address can be quickly blacklisted, and the infected machine can be quarantined.
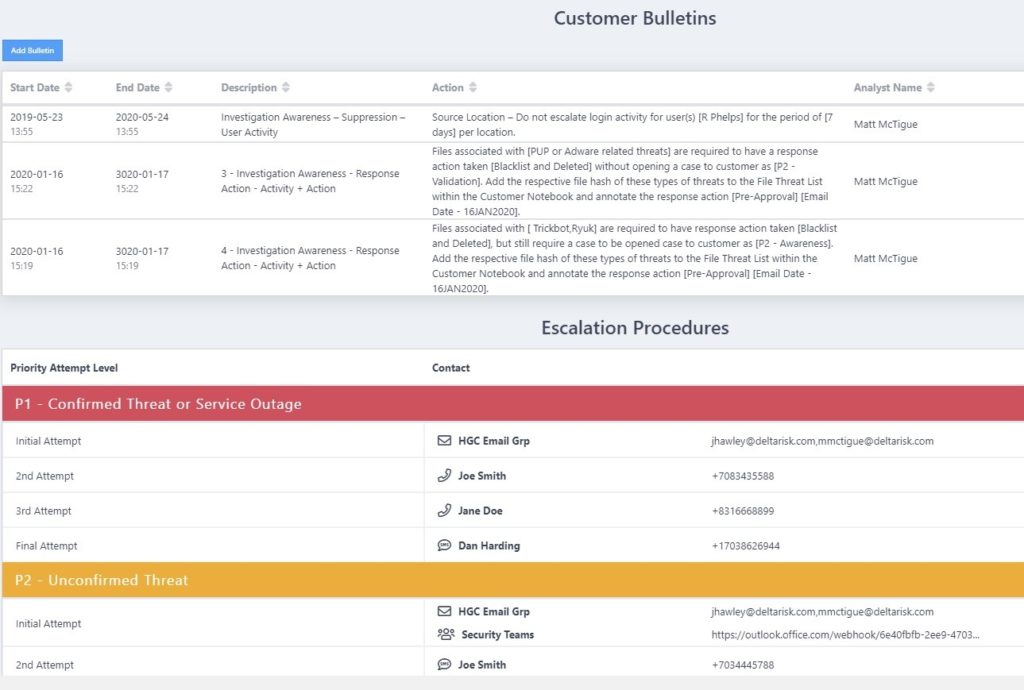
ActiveEye automates more than 95 percent of this process, allowing security teams to see how critical each threat is without having to spend the time investigating every one of them. This is crucial given the volume of alerts that an EDR solution like Carbon Black can generate.
The ActiveEye Virtual Analyst provides orchestration and automation of alerts which can include re-prioritizing alerts, closing alerts that are noise or false positives, or enriching alerts with recommendations for what an analyst should do to address them (and why). This provides the information needed to close an alert or begin the triage process for actual threats (Figure 2).
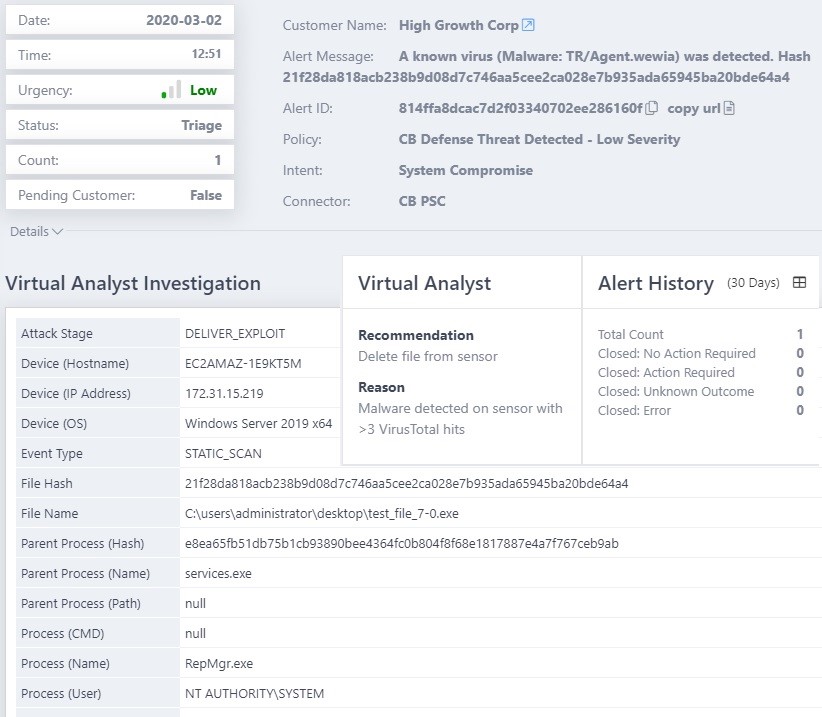
Addressing Endpoint Alerts from within ActiveEye
For VMware Carbon Black Cloud™ Endpoint Standard we’ve taken things a step further with automation that reaches out to the endpoint agent through the Carbon Black API. Our SOC analysts, or an IR team, can take most common actions from within the ActiveEye portal. These automated actions include deleting a hash from a specific device, globally blacklisting or whitelisting a hash, or deleting a hash from all the endpoints in the environment that have the Carbon Black agent (Figure 3).
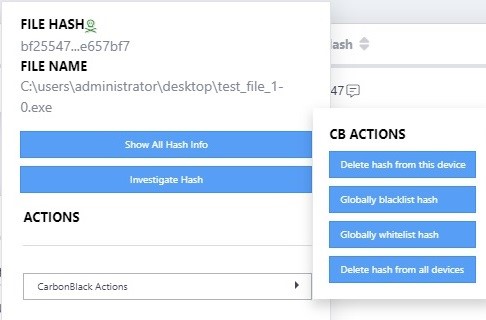
Once we move past the initial stages of IR, ActiveEye transitions to an ongoing operations platform. You can also pull in security events from business applications like Microsoft Office 365 and Google G Suite, as well as firewalls, WAFs, proxies, and other security platforms. This provides a new avenue of threat hunting by combining what Carbon Black identifies with information from other security feeds.
For example, if Carbon Black identifies suspicious activity coming from a specific machine, we could look at the DNS activity of that machine pulled from Cisco Umbrella logs. We could also look at the login activity of the user based on what we can pull in from the Office 365 service connector. These correlations could be found by ActiveEye policies, or when a SOC analyst hunts for threats.
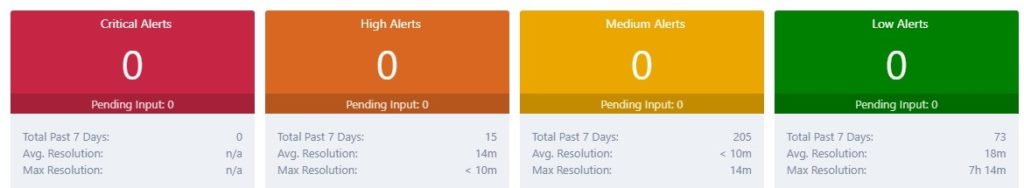
Key Performance Indicators (KPIs) Dashboard
One question that’s always top of mind is whether alerts are being handled quickly and efficiently. The key performance indicators (KPIs) on ActiveEye’s main dashboard (Figure 4) show you just that. The dashboard gives you clear answers about how many alerts have been handled over a certain time period and how quickly they were addressed.
This is important information to have for internal use if you’re a client, and if you’re an IR firm, you can share this data with your customers. With automated reporting and access to real-time environment data, you don’t have to manually collect and compile the information for all the different customer environments you might be working at any given time.
Summary
The ActiveEye portal fills a vital role by gathering multiple security data streams into a consolidated environment, including VMware Carbon Black EDR alerts. It works as a stand-alone platform if you’re managing security for a single organization, and can scale up to address the needs of multiple customers for IR firms. The ActiveEye Virtual Assistant reduces noise and false positives, so analysts can pursue actual threats and focus on proactive threat hunting.
Alerts and critical process information are consolidated, which improves response times and helps security professionals be much more efficient. This impact is amplified for SOC teams and IR teams who are tasked with managing multiple customers at once and tens of thousands of end points and alerts.
