
Public Sector Security
Meet Delta Risk’s Public Sector Team
Delta Risk’s public sector team provides a wide range of professional government cyber security services to many departments and agencies. We work with many government clients, including those that execute critical cyber operations in national and homeland security. We also work with government-funded research institutions. Delta Risk is uniquely qualified to help public sector entities prevent and minimize cyber risks. Our team has the strategic and operational experience to effectively assist government organizations with their cyber security needs. Our experts have developed an impressive track record with military entities, intelligence organizations, and Fortune 500 companies.
Service Offerings

Risk and Vulnerability Assessments (RVA)
Identifying and understanding the risks and vulnerabilities facing your organization is critical to all public sector organizations. Our Risk and Vulnerability Assessment (RVA) process is based on appraising the various technical, operational and business threats and vulnerabilities of a system, and providing remediation recommendations for each of the findings.
Delta Risk’s methodology is built through the DHS RVA program, having supported DHS for the past six years and helping DHS develop and mature this program as one of their key contractors. While our DHS support is based on National Institute of Standards and Technology (NIST) standards, incorporating the Cybersecurity Framework and NIST 800-53 controls, we are flexible to apply other frameworks, such as the International Organization for Standardization (ISO) 27002, HIPAA, or other specific frameworks relevant to your situation.
Our RVAs are customizable to your needs and can include vulnerability assessments, penetration testing, web application penetration testing, controls assessments, wireless assessments, STIG assessments, phishing assessments, social engineering assessments, and others as needed to provide a comprehensive look at the risks and vulnerabilities that exist in your enterprise and business processes.

Penetration Testing
Our penetration testing service provides an assessment of the target system in its ability to resist an attacker. Starting with a vulnerability scan, we attempt to break into the targeted systems without any additional knowledge regarding the systems being assessed.
Our team will replicate attacker tactics according to the NIST SP 800-30 Rev. 1, Guide for Conducting Risk Assessments, based on our assessment of likely attack vectors or previously observed attacks. We will make every attempt to compromise systems that are vulnerable and then use tactics to move laterally to other systems and escalate privileges in order to access more systems. During this phase, we will also search hosts for critical information (PII, PCI, user credentials, certificates, etc.) to demonstrate the potential loss impact from an attacker.
We will finish the assessment by preparing a report that details our specific methodology for successful attacks and provide recommendations for remediating all vulnerabilities discovered. We can also conduct a Red Team Assessment where our testers operate in stealth to test the defense’s ability to detect and stop an attacker.
Incident Response Planning
Security incidents and data breaches can be extremely costly for an organization on many levels. Every public sector agency, no matter the size, must be prepared for any incident, intentional or accidental.
The better you as an organization can plan for a potential incident, the more prepared you are to respond appropriately. Using the NIST SP 800-61 Rev. 2, Computer Security Incident Handling Guide, Delta Risk’s incident response team can assist with incident response planning services that supplement any organization’s existing incident management plans and capabilities.
No matter your organization’s needs, our experienced team will help your organization be prepared to respond to any security incident.
Exercises
Conducting cyber security exercises is invaluable for an organization to evaluate its current security program. Delta Risk uses risk-based and scenario-based approaches that can be tailored to any public sector organization to help identify strengths and weaknesses in your organization’s incident response program and its ability to detect and respond to cyber threats.
From executing single event exercises to building comprehensive exercise programs, Delta Risk will guide your organization to develop a strong demonstrated capability in cyber incident response by simulating real-world events that your organization must respond to.
At the conclusion of the exercise, the team will provide actionable remediation that will improve your organization’s program, helping to detect and respond to incidents faster. The actions taken to solidify program gaps and close capability weaknesses will give your employees a much more effective process by which they can respond to future incidents.

Governance, Strategy, Policy
Our cyber security professionals possess a wealth of knowledge on the cyber domain specifically relating to the executive-level planning and strategy experience needed for today’s public sector organizations at every level.
Whether you are a local government or a federal agency, our senior cadre has the strategic experience to help guide your organization from supporting a new NIST-based governance structure to providing cyber expertise for the Department of Defense (DoD) Cybersecurity Strategy. Our team brings unmatched experience to the table and can access throughout Delta Risk allows us to provide current and responsible guidance to meet your organization’s needs.
How to Order:

Federal, state, and local governments can rapidly buy services from Delta Risk by using the following Highly Adaptive Cybersecurity Services (HACS) Special Item Numbers (SIN) on GSA’s IT Schedule 70:
- SIN 54151HACS
- SIN 132 45
Delta Risk also has two additional GSA SINS:
- SIN 132-50: Training Services
- SIN 132-51: Professional Services
To learn more about how to order go to www.gsa.gov/portal/content/198589Get in Touch
Certified Small Business

Top Secret Facility Clearance

Verify the Strength of Your Information Security Program
Cyber Security Program Assessments
Developing a program, reviewing its effectiveness, and testing program resilience will help ensure your organization has met its compliance obligations.
Our assessments review your current cyber and IT risks, policies, and programs. With this comprehensive analysis, we can identify your program’s strengths and weaknesses to find any security gaps. We can also advise your organization on the optimal solutions for your business based on your unique risks and resource constraints.
Once developed, you need to test the effectiveness of your program in simulated real-world scenarios. Delta Risk offers red-team and table-top exercises tailored to your specific requirements, and developed with our expertise in defending government networks.
As insider threats (i.e., malicious or negligent employees) can also be a major concern for public sector entities, we deliver services directed at managing the human element of security. Delta Risk offers cyber security training and awareness courses for all levels of digital expertise.
Our Customers





Access Services Built Around Your Security Needs
SOC-as-a-Services
Delta Risk’s managed security services efficiently and effectively manage your technical security needs. Our services are scalable to the size, complexity, and risk tolerance of your organization.
Protecting Government Data with Comprehensive Cyber Defenses
Public Sector Breach Response Services
If your organization suffers a breach, or you suspect one has already occurred, Delta Risk offers a variety of services to help you respond, including:
- Hunting for current or undiscovered threats affecting your network,
- Coaching your organization through difficult decisions after a breach, and
- Providing a response team with a host of capabilities to deal with an active threat.
Multi-Faceted Cyber Security Issues Impact Public Sector
Government organizations across the globe must protect and defend their data and networks against persistent cyber threats. No organization is immune to the devastating consequences cyber criminals and sophisticated nation-state actors can cause by accessing a public entity’s sensitive/classified information, intellectual property (IP), and/or personally identifiable information.
Most organizations recognize the threat of a foreign entity gaining access to state secrets or defense matters. There are a myriad of other cyber threats facing public sector organizations, however. For one, countries are actively exfiltrating intellectual property. This not only damages the competitive advantage of private companies, but it can also affect national security.
Identifying Threat Types and Motivations
Malicious cyber actors target governmental organizations because of the vast databases of information they contain. This may include information on residents or extensive personal information on employees. This was illustrated by the U.S. Government’s Office of Personnel Management (OPM) breach.
An organization’s employees could also be considered threats. This threat can materialize as a malicious actor stealing sensitive data, or a negligent employee who inadvertently enables access to files and systems. The sheer number of people employed by the government both directly and as contractors creates additional risk.
- Maintain an Inventory of Information Systems
- Categorize Information and Systems According to Risk Level
- Maintain a System Security Plan
- Implement Security Controls
- Conduct Risk Assessments
- Achieve Certification and/or Accreditation
- Conduct Continuous Monitoring
Failure to meet the requirements of FISMA could result in budget cuts to an agency or termination from a contract for a private government contractor.
Public Sector Compliance – FISMA Overview
In the US, the most important cyber regulation in the public sector is the Federal Information Security Management Act (FISMA), passed in 2002 as part of the E-Government Act, with updates in December 2014.
Similar to industry-specific cyber regulations like those in the healthcare or financial services industries, FISMA requires each federal agency to develop, document, and implement a cyber security program. In addition to all federal agencies, FISMA also applies to state agencies that are administering federal programs. This includes Medicare, Medicaid, unemployment insurance, and private government contractors who meet expansive criteria.
If your organization is using a cloud environment, your cloud service provider (CSP) must also comply with FISMA requirements. The use of such services is reviewed under the government-wide Federal Risk and Authorization Management Program (FedRAMP).
FISMA assigns the role of developing the standards and minimum security requirements to the National Institute of Standards and Technology (NIST), which the Secretary of Commerce approves. The requirements are extensive, encompassing 17 areas of security detailing approximately 205 specific requirements.
Stay Informed on Cyber Security Managed Services
Guide

10 Tips for Selecting an MSSP
In “Top 10 Tips for Selecting an MSSP,” we provide important steps to make the selection process less daunting. Our list of best practices will help you pinpoint the considerations you need to make before making a final decision.
Data Sheet

ActiveEye Managed Security Services Data Sheet
Business is increasingly being conducted on platforms like mobile devices and cloud services, making it difficult for traditional IT and security to keep up. With the frequency and severity of attacks increasing, your organization needs the people, technology, and proven methods to swiftly recognize and respond to the oncoming rush of threats.
Blog

What Defines a Modern SOC-as-a-Service Solution?
The first of a two-part series, we’ll discuss what defines a modern SOC-as-a-Service solution, also known as outsourced or co-managed security operations center (SOC).
Video
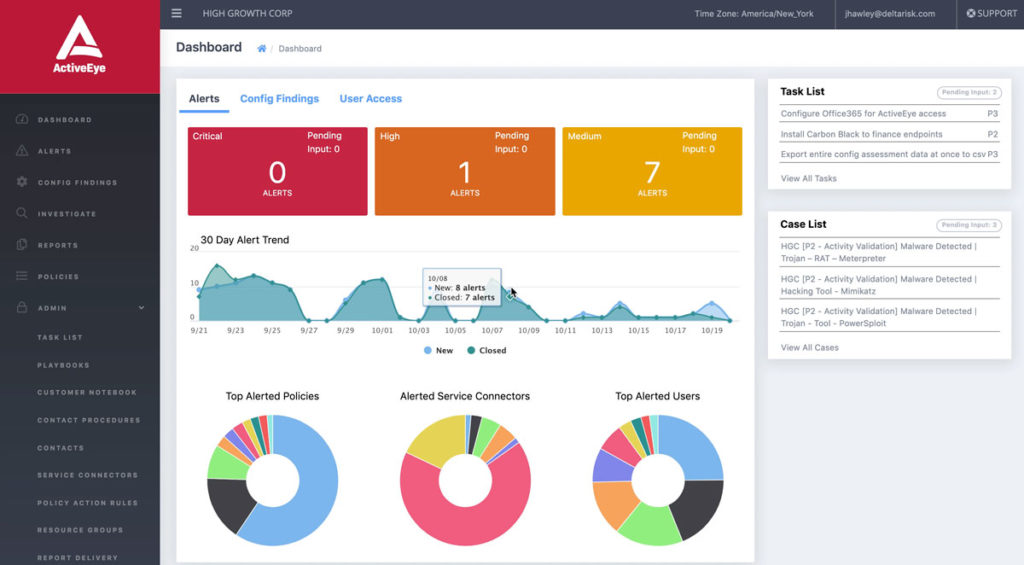
ActiveEye Managed Security Platform Overview
Watch this short demo to learn more about ActiveEye, our modern, cloud-native platform. ActiveEye gives you a transparent view into all security operations center (SOC) activities.